Extension Kit – O365 OAuth setup manual is needed only for Email Notifications and Reporting module in the Extension Kit.
If you want to setup Mail server configuration using Office365 OAuth, then choose Authentication type Office365OAuth and follow this manual to setup and gather needed information from Azure portal.
- Open Azure portal and go to Microsoft Entra ID
- Under App registrations add new registration (for example: Extension Kit)
- Save Application (client) ID and Directory (tenant) ID, as they will need to be added to the Mail Server configuration in Extension Kit
- Under Certificates & secrets add new client secret. After creation, copy your client secret value to use it in Extension Kit configuration. It’s important to copy its value immediately, as later you can’t see and use it again.
- Under your app new registration navigate to API permissions, click on Add permissions.
Go to APIs your organization uses, find Office 365 Exchange Online, and add these permissions:
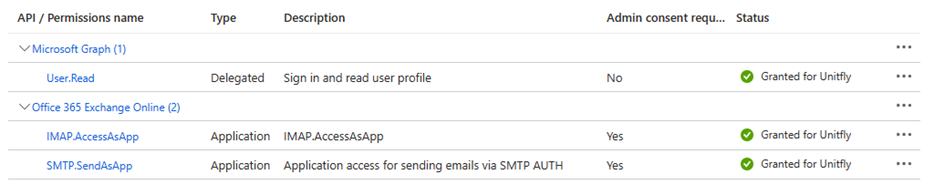
Microsoft Graph, User.Read permission is there by default and you can leave it there.
All added permissions need to be granted by Admin.
IMAP.AccessAsApp – is needed for delivery notifications in the E-mail Notifications module.
6. Next step is then to add new service principal in exchange and add desired user/s permission to that principal Register service principals in Exchange
Once a tenant admin consents your Microsoft Entra application, they must register your Entra AD application’s service principal in Exchange via Exchange Online PowerShell.
To use the New-ServicePrincipal cmdlet, install ExchangeOnlineManagement and connect to your tenant as shown in the following snippet:
Install-Module -Name ExchangeOnlineManagement -allowprerelease Import-module ExchangeOnlineManagement Connect-ExchangeOnline -Organization <tenantId>
If you still get an error running the New-ServicePrincipal cmdlet after you perform these steps, it’s likely because the user doesn’t have enough permissions in Exchange online to perform the operation.
Registration of an Microsoft Entra application’s service principal in Exchange is shown in the following example:
New-ServicePrincipal -AppId <APPLICATION_ID> -ObjectId <OBJECT_ID> [-Organization <ORGANIZATION_ID>]
The tenant admin can find the service principal identifiers referenced above in your Entra AD application’s enterprise application instance on the tenant. You can find the list of the enterprise application instances on the tenant in the Enterprise applications blade in the Microsoft Entra view in Azure Portal.
Get-ServicePrincipal | fl
The OBJECT_ID is the Object ID from the Overview page of the Enterprise Application node (Azure Portal) for the application registration. It is not the Object ID from the Overview page of the App Registrations node. Using the incorrect Object ID will cause an authentication failure. The tenant admin can now add the specific mailboxes in the tenant that will be allowed to be accessed by your application.
The following example shows how to give your application’s service principal access to one mailbox: Add-MailboxPermission -Identity “john.smith@contoso.com” -User <SERVICE_PRINCIPAL_ID> -AccessRights FullAccess
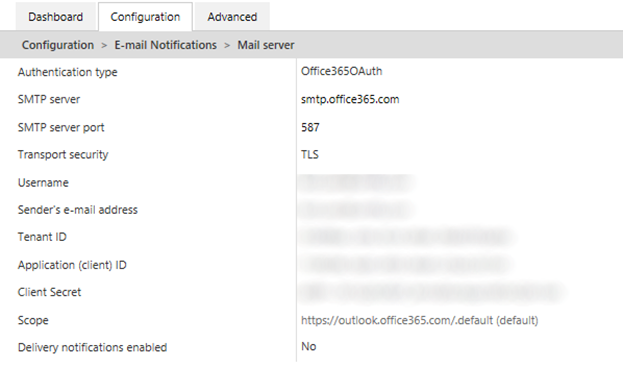
7. Set Extension Kit Mail server configuration
References
Set up OAuth 2.0 client credentials flow – Azure AD B2C | Microsoft Learn
Authenticate an IMAP, POP or SMTP connection using OAuth | Microsoft Learn